Dokploy is a self proclaimed open source alternative to Vercel, Netlify and Heroku. It was founded by Mauricio Siu who also goes by the name of Siumauricio on GitHub.
What does Dokploy do?
With Dokploy, it's easy to create new Docker containers, host websites and microservices, and much more. It allows people who want to rent or run their own servers to deploy their next side project in minutes, removing the need to pay for a managed cloud provider like Vercel.
The Vulnerability
After trying out and even sponsoring Dokploy with a few bucks per month, they released a feature called "preview deployments" and we had to try it! We quickly noticed however that Dokploy immediately deployed any code in a pull request without waiting for a maintainer to approve the deployment first. On top of that Dokploy also commented on the pull request with a link to the deployed code, jackpot!
We found this fishy and decided to create another repo, a simple Next.js app, and enable preview deployments. These preview deployments can also have their own environment variables that can be used to store for example test API keys, so we added some fake API keys for our test. We then opened a pull request with a simple Next.js API route that returns the environment variables and waited. Dokploy immediately started deploying the "scary" code and replied with a public link to access it.
Jackpot!
On December 16th 2024 I sent a direct message to the founder and maintainer of Dokploy on Discord telling them about the possible vulnerability on the same day. They assured me that they would add an option so only whitelisted GitHub accounts can trigger preview deployments, fine right?
No, over 6 months later on the 12th of July we got curious and decided to try again on the newest version to date 24.0. This time a fellow software engineer Iza, CEO of Databuddy, a privacy first analytics provider, came to help us out opening another pull request with identical code. And there it was Dokploy instantly started to deploy the code and just like last time our environment variables were exposed to anyone.
Why are you making this public?
In May 2025 we asked about an update on the vulnerability in their public Discord server, we understand that we shouldn't have brought this up in public before talking to the founder again in direct messages, but we wanted to make sure the users were at least warned about the potential security risk. After being told that the temporary solution is to make your repository private and that this wasn't a vulnerability but a bug. And given the fact that it has been at least another 1-2months after asking again without a fix or public announcement warning users we decided to publicly share this.
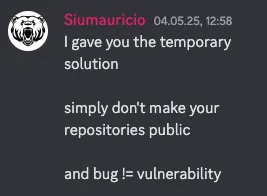
Checkout the original response by the creator!
Conclusion
Our goal isn't to destroy Dokploy's reputation. In fact, we still believe in the project. However, we also want to ensure that Dokploy's users stay safe. If they don't want to announce the vulnerability or fix it, then we have to take a different approach to warn users about the risk. We are unsure if this issue affects other git providers and the whole scope of the vulnerability. Based on what we saw we can only say for sure that public repositories on GitHub using Dokploy preview deployments are vulnerable. We do however believe that other git providers are also impacted and that this vulnerability might be seen as a remote code execution vulnerability. We hope Dokploy can fix this vulnerability asap and will follow up with an update if they do. In the meantime verify that you have turned off preview deployments or make your repositories private. If you still need secure preview deployments we can recommend Vercel and Netlify, their free tiers are really generous and enough for small scale projects.
Update July 14. 2025
We submitted the vulnerability to Dokploy again, this time through GitHub's security tab. Read more here. A day later on July 14. 2025 a fix has been merged in #2192 and published in v0.24.3. If you use Dokploy preview deployments please update to this version or newer depending on when you are reading this!
